Authorization
In this article, you will find authorization-related basic concepts used in the documentation.
CKEditor Cloud Services have a few authorization methods, and each of them is suited for a given communication way. To find more detailed information, please check the linked articles.
The diagram below shows what authorization methods are available and where given operations need to be performed.
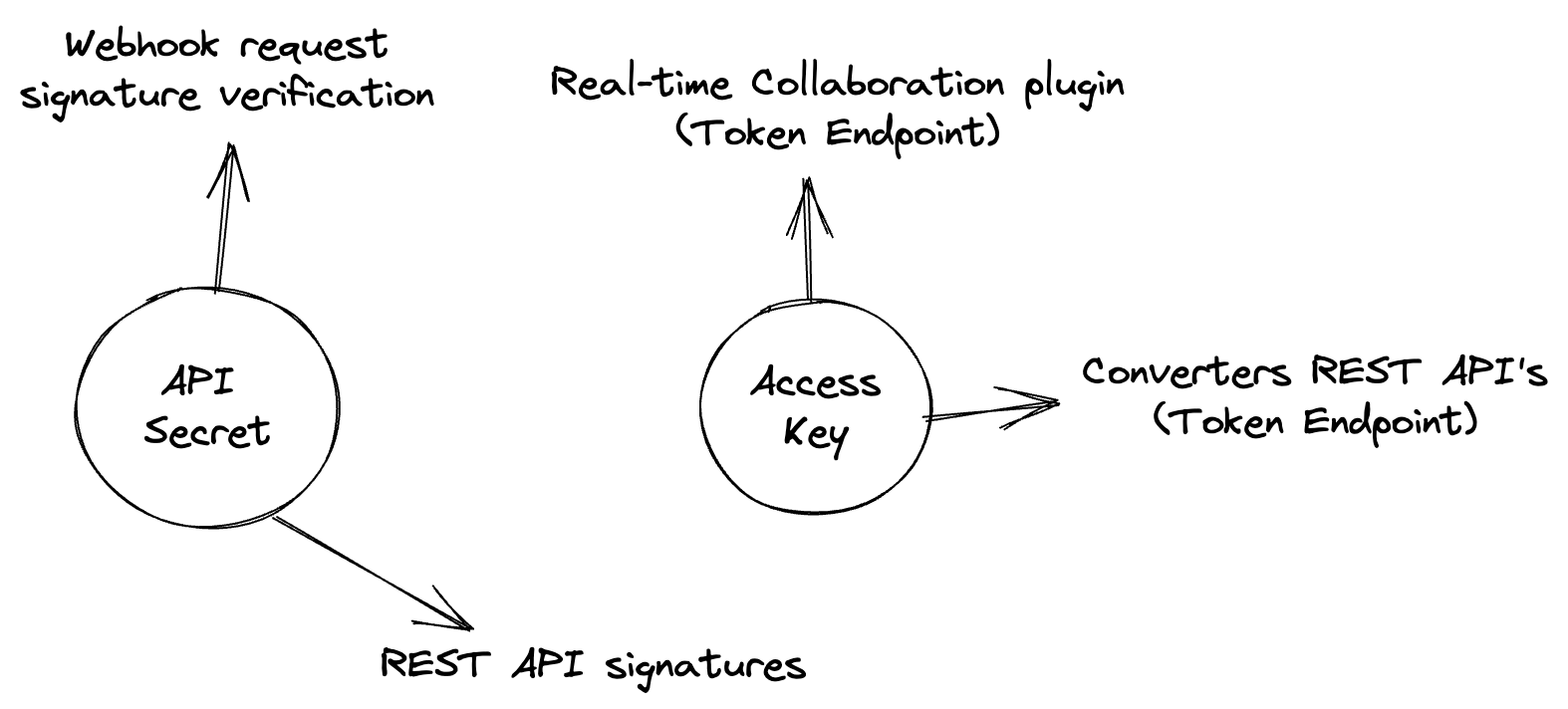
An API secret is a secret used to generate a signature for requests made to the REST API.
It is also used to verify webhooks requests.
API secrets can be managed through the Customer Portal, or through the Management Panel in case of On-premises installations.
An Access Key is a key used to generate signed tokens.
Access Keys are generated in the Customer Portal or in the Management Panel in case of On-premises installations.
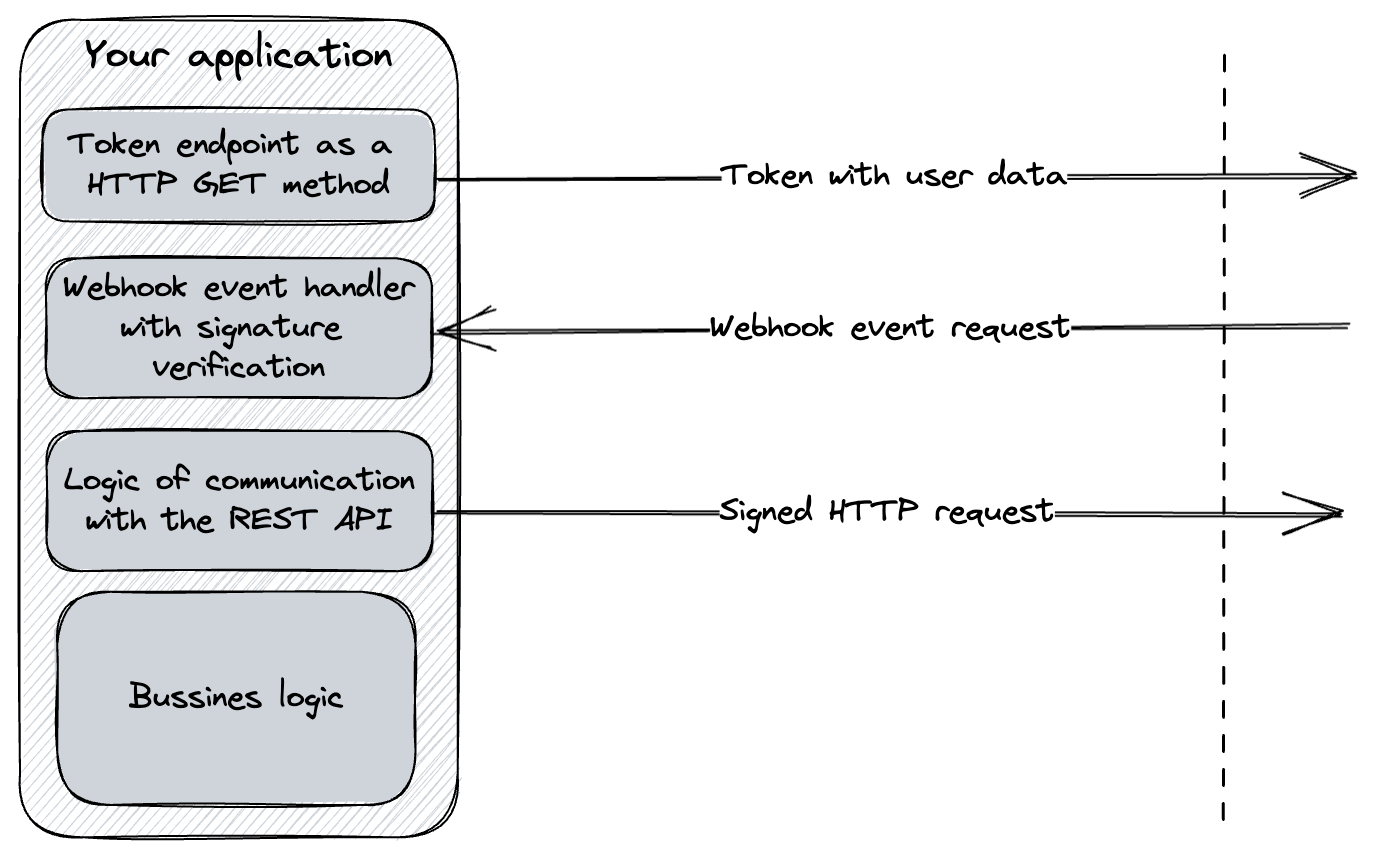
An endpoint created by a customer which returns a token. It needs to be created by customers and placed in the customers’ application. Thanks to that, a customer has the full ability to control the user data and privileges sent.
You can read more about the token endpoint in the Token endpoint guide.
It is returned from a Token endpoint. In the payload, it contains all user data and roles and permissions of the user to a given document. Based on a sub property of the token, the usage of the application is billed.
You can read more about tokens and their generation in a dedicated section.